How to: |
Once you have decided which type of authentication to use and before you can enable external authentication, you must configure the properties that enable Managed Reporting to communicate with the external directory.
You can configure these authentication properties in the WebFOCUS Administration console by going to the WebFOCUS Welcome page (http://hostname:port/ibi_apps/, where hostname is the host name of the machine on which the WebFOCUS Client is installed, and port is the port on which it listens), and clicking the WebFOCUS Administration Console link.
Log on to the WebFOCUS Administration Console as an administrator (default ID is admin with no password). Click Configuration and click External Directories in MR Security Settings.
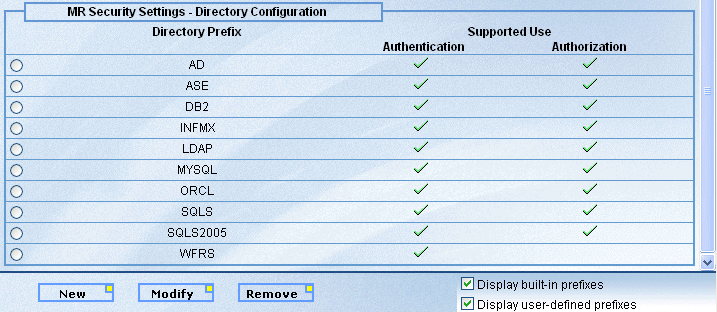
To configure properties for a specific external directory, double-click the prefix for that directory, which opens the Modify Settings window. Alternatively, select the radio button in front of the directory prefix and click the Modify button at the bottom of the screen. The built-in directories that are described in this section are listed in the following table.
|
Directory |
Prefix |
|---|---|
|
Active Directory |
AD |
|
LDAP |
LDAP |
|
WebFOCUS Reporting Server |
WFRS |
Note:
- The prefix is used to identify the set of properties required to connect to an external directory and also as the means to identify which set of properties is currently loaded for authentication. You can add directories or alternate versions of the same directory (by creating a new prefix) to the list of available directories. For information, see How to Create a Copy of Your Directory Settings.
- The relational DBMS directory prefixes that are shown on the screen but are not listed in the table are not supported for external authentication unless Managed Reporting is also configured to use them for external authorization. Therefore, for instructions about these prefixes, see Configuring Managed Reporting for External Authorization.
Now you can configure the appropriate authentication properties as described in the following sections.
Configure these settings if you selected the WFRS directory prefix and clicked the Modify button:
-
Update
the hostname:port placeholder with the appropriate values.
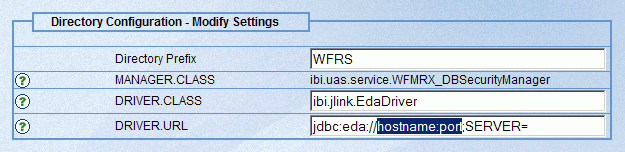
- If the server is on MVS, supply the appropriate service name after the SERVER= keyword.
- If the server
is on IBM UNIX System Services (USS), you need to append a code page
setting to the URL as follows:
jdbc:eda://hostname:port;SERVER=servername;code_page=437
-
Click Save.
If your WebFOCUS Reporting Server is configured for operating system security, you must start the Reporting Server in SECURITY ON mode. However, if your Reporting Server is configured for LDAP or DBMS security, you must start it in the appropriate security mode. For information about configuring the Reporting Server for these security modes, see Chapter 2, Server Security, in the Server Administration for UNIX, Windows, OpenVMS, IBM i, and z/OS manual.
When using this option, the Reporting Server credentials of each user are preserved in their individual session object on the Web-tier. By default, this session expires after 30 minutes of inactivity, resulting in a subsequent prompt for the Reporting Server credentials. You can extend the timeout period by editing the <session-timeout> attribute found in the WebFOCUS Web application deployment descriptor (web.xml).
Note: If the prefix you are saving is named under Current Settings on the MR Security Settings - Directory Configuration panel, you will be prompted to reload the repository driver. Click OK.
To understand what happens when you configure these settings, see Internal Processing for Reporting Server Authentication.
For more information, see the online help in the IBI_EDACONNECTOR setting.
Now that you have configured your authentication properties, you can enable external authentication using this prefix. To do so, remain logged on to the WebFOCUS Administration Console and follow the instructions in How to Enable External Authentication.
Configure these settings if you selected the LDAP or AD directory prefix and clicked the Modify button.
The WebFOCUS Administration Console places the following properties in mrrealm.cfg when you choose Active Directory or LDAP for authentication.
-
Edit
the following properties to configure LDAP or Active Directory authentication:
- MANAGER.CLASS
-
Is set to ibi.uas.service.WFMRX_LdapSecurityManager when you select LDAP or Active Directory as your authentication directory. This property cannot be edited.
- REPOSITORY_MANAGER.CLASS
-
Is set ibi.uas.service.WFMRX_LdapRepositoryManager when you select LDAP or Active Directory as your authentication directory. This property cannot be edited.
- HOST
-
Is the host name or IP address of your directory server and port on which the directory server listens. For example, server1:389. If you are authenticating to Active Directory, you should consider specifying the host that runs your Global Catalog, which is configured on port 3268 by default. You must specify the Global Catalog host/port when your users are in more than one domain. You can also specify multiple servers for failover support using a comma-delimited format. For example, server1:3169,server2:4310.
- SECURECONNECTION
-
Determines whether the connection is encrypted. A value of false means no encryption. A value of true means SSL encryption is used. Typically, SSL requires additional setup on the directory server (for example, a certificate). For more information, see your directory server documentation. You may also need to register the SSL certificate in your directory with the JVM running your application server, especially if it is a self-signed or expired certificate.
For more information, see WebFOCUS Encryption Features.
- REQUIRECREDENTIALS
-
Specifies whether to perform an anonymous or credential-based search for the user in the directory as a preliminary step in authenticating the user. The default value for LDAP is false, and the default value for Active Directory is true.
For example, a user John Doe enters the user ID JD123 and his password on the Business Intelligence Dashboard logon page.
If REQUIRECREDENTIALS=false, the Realm Driver first performs an anonymous search to locate the distinguished name (DN) of John Doe. For example, "cn=Doe\, John,ou=People,dc=informationbuilders,dc=com". Next, the Realm Driver performs an LDAP bind with the DN and password of the user in order to authenticate him.
If REQUIRECREDENTIALS=true, the first connection is made with a DN with sufficient rights to search the directory and locate user entries of a service account.
Note: Active Directory does not allow an anonymous search.
- SECURITY.PRINCIPAL
-
Contains the DN of a service account with sufficient access rights to locate user entries in the directory. This value is used only when REQUIRECREDENTIALS=true.
- SECURITY.CREDENTIALS
-
Contains the password of the service account. This value is used only when REQUIRECREDENTIALS=true.
- USER.BASE
-
Specifies the root DN where the user search starts. For performance reasons you should set this value as close as possible to your user entries. The default value for LDAP is ou=People,dc=domain,dc=com, and for Active Directory is cn=Users,dc=domain,dc=com. You must replace this with an appropriate DN for your directory.
- USER.SCOPE
-
Specifies the scope of the search. Valid values are:
subtree indicates that the scope is a subtree rooted at the start node. This is the default value.
onelevel indicates the immediate children of the start node only.
- USER.CLASS
-
Specifies the object class used when searching for user entries. The default value for LDAP is inetOrgPerson, and for Active Directory it is User.
- USER.ATTRIBUTE
-
Specifies the LDAP attribute used when searching for user entries. The default value for LDAP is uid, and sAMAccountName is the default value for Active Directory.
One possible reason to change the default value would be to allow users to log on to Managed Reporting with an e-mail address instead of user ID. In this case, you might change the value to mail (if this corresponds with the name of the appropriate attribute in your directory).
You may also want to change this when your Active Directory includes several child domains. In this case, there can be two people with the same ID. You can change the property to userPrincipalName so that users are required to present their ID to Managed Reporting in a domain-qualified (for example, jt01234@ibi.com) format.
-
After
editing the properties, click Save to save the
values or Cancel to leave them as they were
before.
Note: If the prefix you are saving is named under Current Settings on the MR Security Settings - Directory Configuration panel, you will be prompted to reload the repository driver. Click OK.
Now that you have configured your authentication properties, you can enable external authentication using this prefix. To do so, remain logged on to the WebFOCUS Administration Console and follow the instructions in How to Enable External Authentication.
Optionally configure these settings if you selected the LDAP or AD directory prefix and you want to take advantage of LDAP connection pooling. Your servlet container must use Sun Java 1.4.1 or higher. For more information on these settings, refer to the Sun Java documentation.
- POOL.ENABLE
-
To enable the connection pool feature, set this property to true and adjust the other POOL properties as desired. The default value is false.
- POOL.PROTOCOL
-
Defines which types of connections are taken from the pool. The default value is plain, which means that only non-SSL connections are drawn from the pool. You can change this to ssl or to plain ssl to alter the behavior.
- POOL.INITSIZE
-
Defines the initial size of the connection pool. The default value is 1.
- POOL.MAXSIZE
-
Defines the maximum size of the connection pool. The default value is 0, which means no limit. If the limit is reached, the Realm Driver waits for the period specified by POOL.TIMEOUT and then returns an error.
- POOL.PREFSIZE
-
Defines the preferred size of the connection pool. When specified, connections are added and idle connections are removed to achieve value specified. The default value is 0, which means no preferred size.
- POOL.TIMEOUT
-
Defines how long in milliseconds the Realm Driver waits for a connection from the pool. This is initially set to a value of 60000 in the configuration file (one minute). A value of 0 means no timeout.
-
When
you open the properties window for a directory prefix, you can supply
a different value in the Directory Prefix field. For example, if
you selected WFRS, you can create a new prefix, such as WFRSTEST.
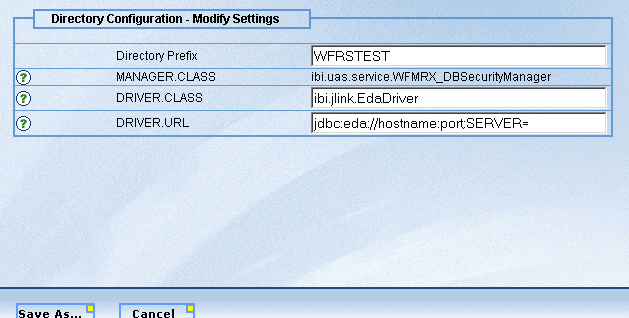
In this case, the Save button becomes the Save As button.
- Click the Save As button to make a copy of the directory settings under the new directory prefix.