How to: |
You can enable SSL for the HTTP Listener to encrypt all traffic between the server and any client application, such as the WebFOCUS Client, a remote server, or a cluster server.
- From the Web Console menu bar, choose Workspace, then Configuration/Monitor.
-
Right-click HTTP under Special
Services and Listeners, and select Properties.
The Agent Configuration page opens.
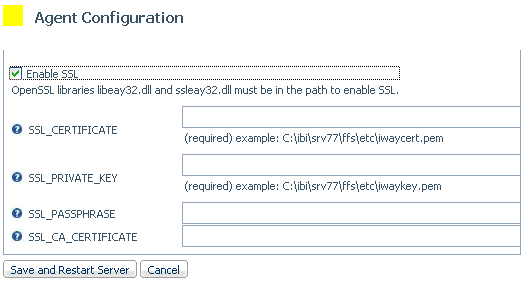
- Open the Advanced pane, scroll down, and check Enable SSL. Note that OpenSSL libraries libeay32.dll and ssleay32.dll must be in the path to enable SSL
-
Enter the following values:
- SSL_CERTIFICATE
-
Contains the certificate chain in order, starting with the certificate for the listener and ending with the root CA certificate. Each of these entries must be in PEM format.
Note that the administrator at the installation site must acquire valid security certificates (self signed or commercial).
- SSL_PRIVATE_KEY
-
Defines the file that contains the private key of the listener. It must correspond to the public key embedded within in the certificate and must be in PEM format.
- SSL_PASSPHRASE
-
If the file defined in SSL_PRIVATE_KEY is encrypted, a passphrase must be provided here to decrypt the private key.
- SSL_CA_CERTIFICATE
-
Defines the name of a file containing a trusted CA certificate in PEM format. It is used to verify the client certificate. If the client fails to send a certificate or verification fails, connections are rejected. More than one CA certificate may be present in the file.
- Click the Apply and Restart Server button.