In this section: |
A security provider is used to authenticate the incoming connection. When a security provider is configured, it is added to edaserve.cfg as a security provider block. Multiple security providers can be configured, in which case the security_provider attribute will consist of a comma-separated list of security providers. The first one on the list is the primary provider.
The security provider can be of several types:
- OPSYS. Users are authenticated against the native OS security repository, such as the windows domain controller, z/OS RACF/ACF2, UNIX password files or other operating system security products using the native OS API.
- LDAP. Users are authenticated against an LDAP server or active directory using the LDAP API.
- DBMS. Users are authenticated by connecting to a DBMS such as Oracle, SAP, or DB2.
- PTH. Users are authenticated against a list of users kept internally by the server in the admin.cfg configuration file.
- CUSTOM. Users are authenticated using a custom procedure.
Initially, when the server is installed, EDAEXTSEC is not set and no other security provider is configured. Under these conditions, the server, by default, will start in OPSYS security mode if it has sufficient privileges for operating system security. If it does not have sufficient privileges, it will start in security OFF mode.
If you want to use a PTH, LDAP, DBMS, or CUSTOM security provider, you must configure it on the Web Console Access Control page. When you configure one of these security providers, the server edits the edaserve.cfg file to add a block for the new security provider. You can then use the Web Console to change to this provider. In response, the server sets the security_provider attribute in edaserve.cfg to this provider name, after which this provider is considered the primary provider and defines the security mode of the server.
You can configure multiple security providers, and the server will add multiple provider blocks in edaserve.cfg. When multiple providers are chosen to be active, the security_provider attribute in edaserve.cfg is set to the list of active providers. In this case, the first provider on the list is considered to be the primary provider and defines the security mode for the server.
EDAEXTSEC can be set to one of two values: OPSYS or OFF. These values can be used to override the security provider identified by the security_provider attribute. The server uses the following information to determine the mode in which it should start:
- If EDAEXTSEC is not set and:
- The security_provider attribute is set in edaserve.cfg, the server starts in the security mode that is specified by the security_provider attribute.
- The security_provider attribute is not set, the server starts in OPSYS security mode if it has sufficient privileges, and in OFF security mode if it does not have sufficient privileges for OPSYS security.
- If EDAEXTSEC is set to:
- OFF, the server starts with security OFF, regardless of the security_provider name set in edaserve.cfg.
- OPSYS, the server starts with security OPSYS, regardless of
the security_provider name set in edaserve.cfg. If the server does
not have sufficient system privileges to start in OPSYS mode, it
will fail with the following error:
(EDA13171) UNABLE TO START SERVER
An example of configuring multiple providers is having two distinct LDAP providers configured against two separate LDAP servers that can contain different users and different groups.
One provider is considered the primary provider, and for other providers the user name is prefixed with the provider name, for example LDAP1\usera. Note that users (or groups) from two providers that have identical names (such as LDAP1\usera and LDAP2\usera) are considered different security subjects and can be given different privileges and profiles.
At login time, a user needs to select the security provider name in addition to userid/password.
Note that OPSYS providers can be configured with other security providers. On Windows multiple Windows domains act as different security providers and users. For example, domain1\usera and domain2\usera are not identical.
Security providers LDAP, DBMS, PTH, and CUSTOM must be configured from the Web Console Access Control page.
Note: NLS characters are supported for user ID, group name, password, and domain name on the Web Console Access Control configuration pages.
To switch to security LDAP, DBMS, or CUSTOM, you first need to add a new provider under the appropriate security provider on the Access Control tree. When you add a new provider, the server updates configuration file edaserve.cfg with provider blocks named LDAP_PROVIDER, DBMS_PROVIDER, or CUSTOM_PROVIDER. These blocks are inserted with all attributes that apply to the provider type between BEGIN and END dividers.
Security PTH is available for configuration immediately after installing the server. There is no need for the additional step of creating a new provider as is needed for LDAP, DBMS, and CUSTOM. Once the PTH security provider is configured, you can start adding new PTH users and PTH groups, and you can assign PTH users to PTH groups.
Security provider CUSTOM supports using non-standard security storage. You can create DBMS tables to store users, groups, and passwords. You must then write procedures to read these tables and perform the basic security tasks. This security mechanism has to be created prior to configuring the CUSTOM security provider and must be available when the CUSTOM provider is added to the server provider configuration. It must perform the following standard security tasks:
- Retrieve the user ID and its password to authenticate the user on connecting to the server.
- Retrieve the list of users and groups on user and group registration.
- Retrieve the list of users in each group.
- Retrieve user membership in all available groups.
Once the provider is added, you can change security providers from the Access Control page. Right-click the Security Providers folder and select Change Provider to switch to a newly added provider. At this point, edaserve.cfg is updated with the security_provider attribute that specifies the provider name.
Multiple security providers can be configured. When you configure OPSYS as one of multiple security providers, the server has to be authorized to run security OPSYS, and it needs to have a valid OS user ID and password for starting an agent. The Change Provider page requires you to enter valid OS credentials when you configure OPSYS as one of multiple providers:
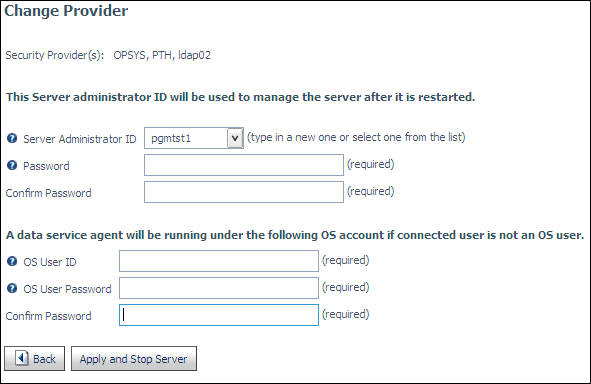
When you configure multiple providers on the Change Provider page, you choose one to be primary. Check boxes are available for assigning the other providers as secondary providers. The primary provider defines the security mode in which the server is running.
During connection to the server, all primary-provider users are connected with a one-part user ID such as User1 or User2. All secondary-provider users connect with a two-part name consisting of the provider name and the user ID, for example, MyLDAP/User1 or MyDBMS/User2, where MyLDAP or MyDBMS is the name of a configured secondary provider.
This naming convention is also used when users and groups are registered to server roles. Users and groups of the primary provider are registered with a one-part name, and users and groups of all secondary providers are registered with a two-part name. If the PTH provider is a secondary provider, PTH users and groups are registered (and used on connection) as PTH/userid and PTH/groupid.
The following is an example of a security_provider attribute and security provider block for starting the server with security LDAP (provider name MyLDAP):
security_provider = MyLDAP LDAP_PROVIDER = MyLDAP BEGIN ldap_host = ldaphost ldap_port = post ldap_secure_connection = n ldap_user_base = dc=ibi,dc=com ldap_user_scope = subtree ldap_user_class = person ldap_user_attribute = uid . . . END
The following is an example of a security_provider attribute and security provider block for starting the server with security DBMS (provider name MyDBMS):
security_provider = MyDBMS DBMS_PROVIDER = MyDBMS BEGIN security_dbms = MSSSQL security_connection =CON01 END