The new feature for LDAP authentication provides additional capability for iWay Service Manager(iSM) to authenticate against LDAP and associate an LDAP iSM role to the user.
iWay Service Manager includes a built-in role for an administrator that allows for complete management and control of iSM from the Web Console. Other roles may be added from the Web Console to limit access and management of iSM.
To implement LDAP authentication for the iSM Web Console, each of these roles need to be added to an LDAP /Active Directory configuration as Groups and then associated to users. Optionally, an LDAP attribute like title may be associated to a role like ism.admin.
The built-in administrator role is;
- ism.admin
Additional roles will need to be defined in the iSM Web Console and also in LDAP. The following procedure describes the required configuration for LDAP and iWay Service Manager.
This section describes how to set up an LDAP group, how to setup and configure iWay Service Manager, and how to add additional Server roles in iWay Service Manager.
This section describes the LDAP group setup for iSM roles. The following steps describe creating an LDAP group based on the iWay Service Manager role and a common name (cn) that is the iSM role. Subsequently adding LDAP members to the group. For example, the LDAP group for the built-in iSM administrator, ism.admin will have a CN=ism.admin.
-
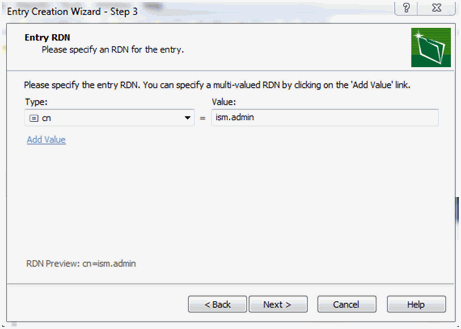
Create a new LDAP Group for ism.admin and set
cn=ism.admin, as shown in the following image.
-
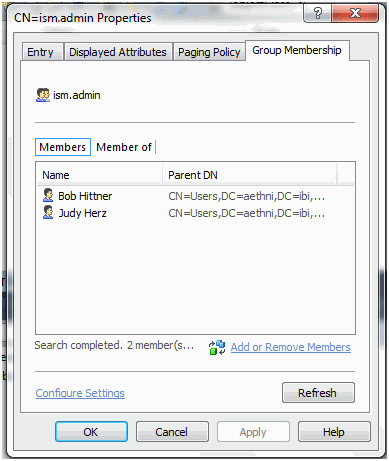
Add LDAP users as members to the LDAP Group ism.admin,
as shown in the following image.
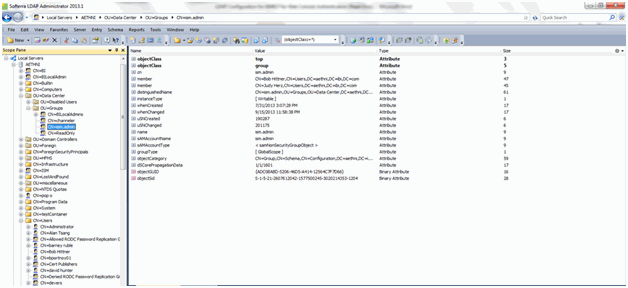
The LDAP Group ism.admin and the associated members of the group can be viewed in the scope pane, as shown in the image below.
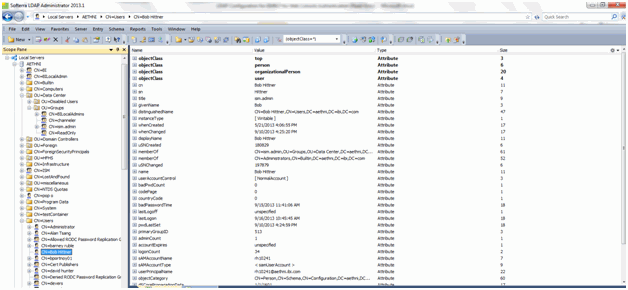
LDAP User screen showing the example used earlier, Bob Hittner, is a member of the ism.admin LDAP Group, is displayed in then image below.
The following section describes the steps to configure iSM to access and authenticate against LDAP. The following steps describe how to create an iSM Directory provider and an authentication realm.
-
To create an iSM Directory Provider to access
the LDAP directory, login to the iSM Web Console. Click the Server Link, then
click Directory Provider.
The Directory Providers: LDAP dialog is displayed, as shown in the following image.
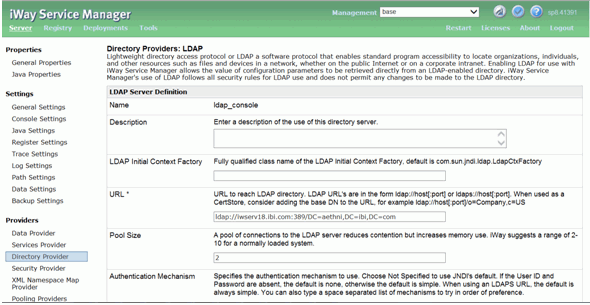
- Update all the required fields for the LDAP Directory Provider, including the LDAP URL, and Base DSN fields.
-
Click the Authentication Mechanism drop-down and select Simple.
Add the User ID and Password for LDAP, as shown in the following
image.
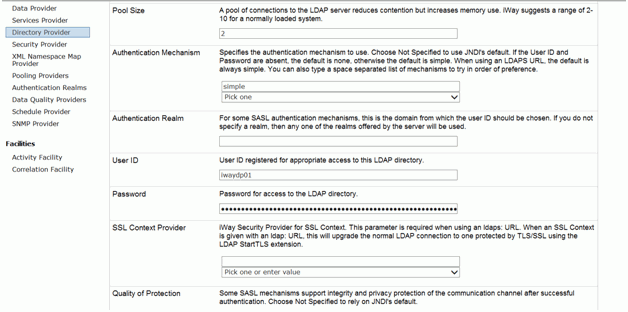
-
Click Add. Test for successful
connectivity. If the connection is successful, the following dialog
is displayed.
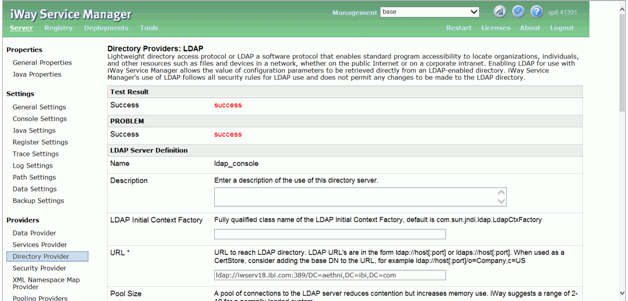
- To add the Authentication Realm, click Authentication Realm under Providers.
- Click New.
-
In the Authentication Realm dialog, Select ldaprealm from
drop-down in the Realm Type field. Enter a name, and select the
configured directory provider in the LDAP Provider field, as displayed
in the following image.
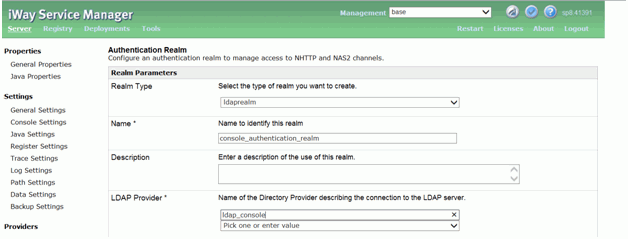
- in the Search User Subtree drop-down, select true.
-
In the User Search Filter field, enter sAMAccountName={0},
as shown in the following image.

-
Enter Role based information as follows:
- Role Base Context: OU=Groups,OU=Data Center.
- Search role Subtree: Select true from the drop-down.
- Role Search Filter: Enter member={0}.
- Role Attribute: Enter cn.
- Click Finish.
-
To update iSM Console Security, Click Management,
as shown in the following image.

-
Click Servers.
The Server creation and management dialog is displayed.
-
Click the configuration name that will be using the LDAP
authentication, as shown in the following example.
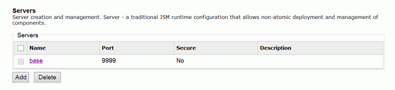
-
Under Console Attributes, update the Authentication Realm
parameter to use the authentication realm created above, as shown
in the following image.
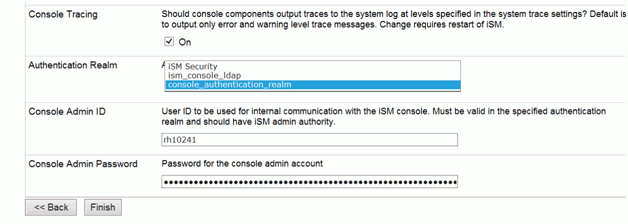
-
Enter the LDAP User ID and Password that is associated
with ism.admin LDAP Group.
Optionally, check Console Tracing to debug LDAP authentication issues.
- Click Finish.
- Restart iSM and login to the iSM Web Console
Note: To debug LDAP authentication problems, start iSM from a Windows Command Prompt window and start iSM using the following command and option -u; iway61 base -u.
The setup of LDAP connection and authentication for iSM is complete.
The following section describes how to define additional iSM roles.
- Click Management and then Server Roles.
-
Click Add.
The Server roles page is displayed.
- In the Name field, enter ReadWrite.
-
Select the allowable actions, as shown in the following
image.
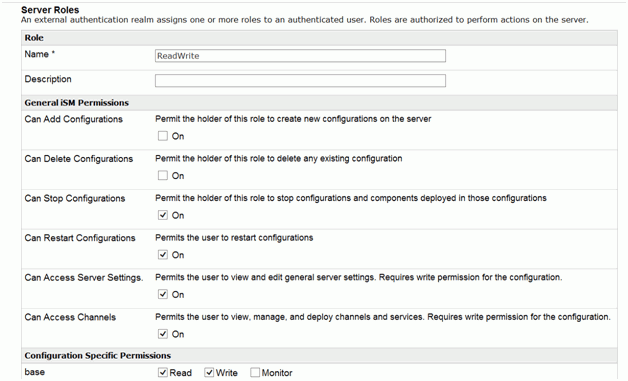
-
Follow the steps under LDAP Setup and Configuration to add the LDAP Group for the ReadWrite role.
Note: The name of the iSM role must match the name of the LDAP group i.e. iSM role = ReadWrite LDAP Group = ReadWrite. They are mapped by using the same name.
- Restart iSM and verify new role.
To troubleshoot LDAP authentication in iSM, perform the following:
- Enable Console tracing as described in step 16 of How to Setup and Configure iWay Service Manager .
- Click on the Server link and click Trace Settings. Enable Debug and Deep,
as shown in the following image.
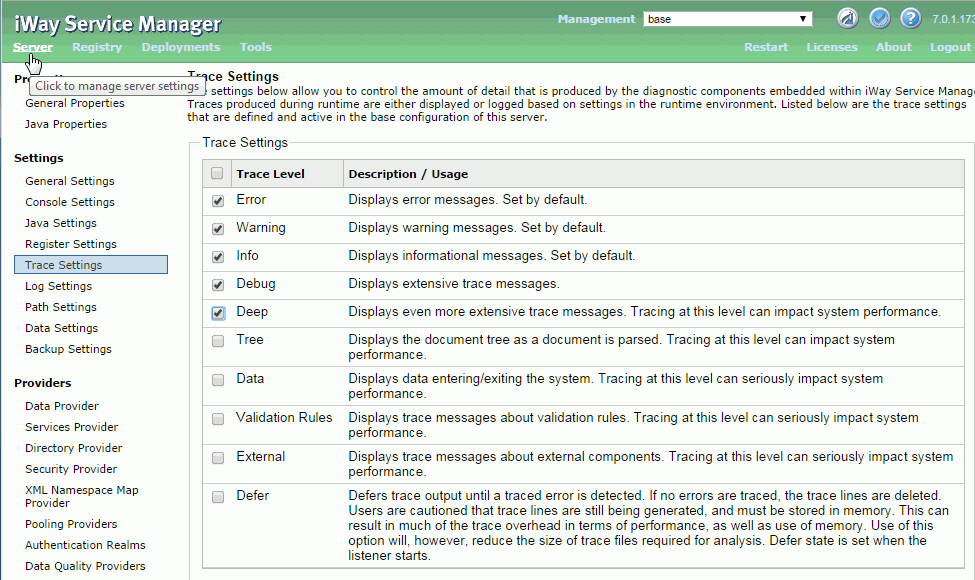
- Try logging in to the iSM console(configuration)
- Collect log files from the iSM config log directory in the following
path: \\iwayhome\config\base\log. Review the most
recent log file.
For example:
DEEP (console) LDAP Realm, entry found for csswxz with dn CN=CSSWXZ,CN=Users,DC=eda,DC=csseda,DC=com DEEP (console) LDAP User role name cn search DEEP (console) LDAP Realm, retrieving values for attribute cn DEBUG (console) LDAP Realm, csswxz authenticated successfully DEEP (console) LDAP Realm, getRoles(CN=CSSWXZ,CN=Users,DC=eda,DC=csseda,DC=com) DEEP (console) LDAP Realm, retrieving values for attribute cn DEEP (console) LDAP Realm, Returning roles: CSSWXZism.admin DEEP (console) LDAP Realm, Closing directory contex
Note: The ism.admin role may seem joined to another role(CSSWXZism.admin). This is expected behavior. Check to make sure that the ism.admin role, or any other role you assign, exists under Returning roles in the log file.