Security policies can be used to secure the server during
run time. For example, if a security policy, such as dictionary
and process flow signing is set when a runtime application is distributed,
the server requires that the dictionary and any process flows to
be run are signed using XML Digital Signatures. At startup, if the
dictionary is not signed, the server will not start. An appropriate
error message will be issued. Once running, any process flows to
be run must be validly signed. Any attempt to load and run an unsigned or
modified flow will be rejected. This protection applies to all channels.
In addition, the iWay Service Manager console is disabled, as required.
Application-specific consoles work through the standard HTTP channels,
and are of course available.
Management of the dictionary signature is automatic. A validly
signed dictionary must be distributed to customers. Doing this simply
means taking the dictionary to be run from the development system.
No further preparation or action is necessary.
Process flows need to be signed individually before they are
packaged for distribution. The server manages signing keys and it
considers two types of files: dictionaries and process flows. Each
type uses a unique key pair. The server automatically selects the
proper key for signing and validating configuration files based
upon the type of file.
x
The set of ACLs for the system are its policies. Policies
are stored in a policy file in the config area. The candidate schema
layout shown below is for discussion and clarification only.
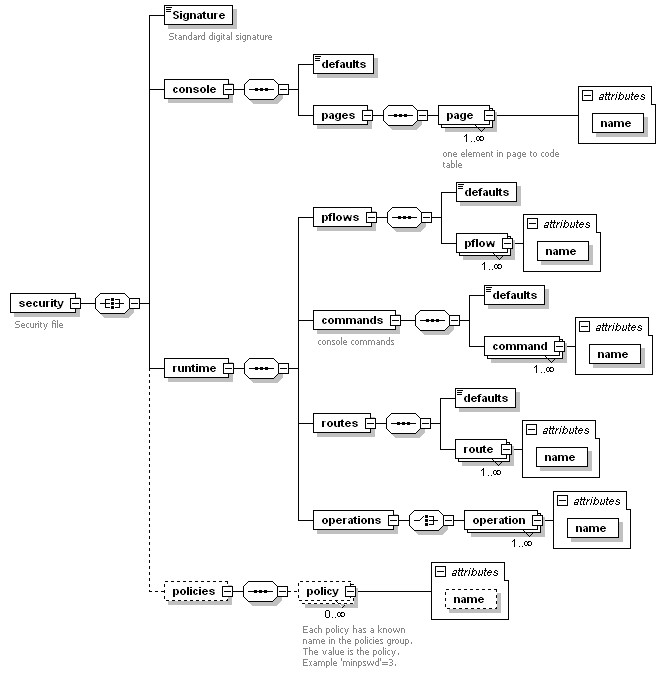
The file stores the policies under which the server operates.
It is not clear at this time whether the policies for run time differ
by configuration. Should it be so decided, the policy layout will
be changed. Each section has a default area in which the access
role for any object of that section that is not named is stored.
x
Policies are values that control server actions. An
example is minpswd, which controls the minimum length of passwords.
Policies are carried in the file, and can be checked as needed in
the server. The following table lists a selection of policies:
|
Name
|
Use
|
Comments
|
|---|
|
minpswd
|
Minimum password length
|
Does not apply to passwords recorded for
other systems. For example, FTP.
|
|
signpflow
|
Should all pflows be signed
|
Move from license
|
