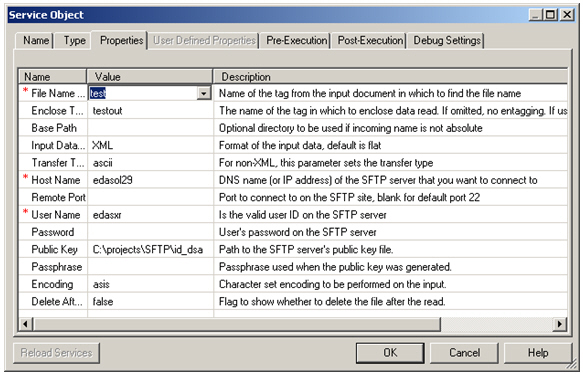
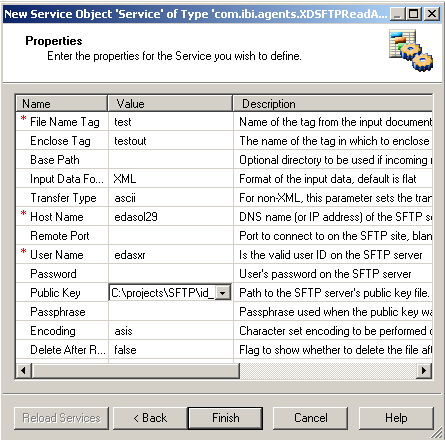
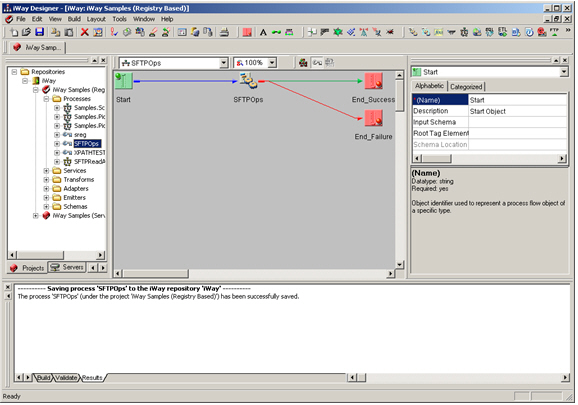
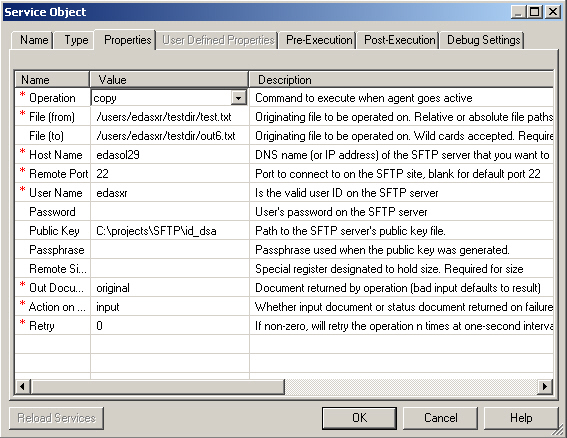
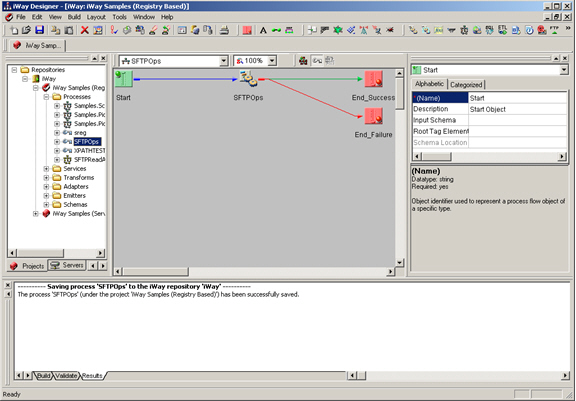
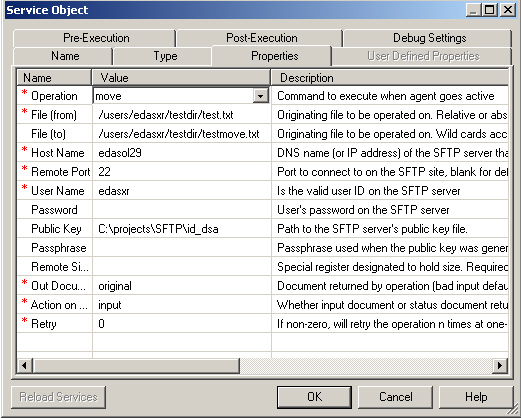
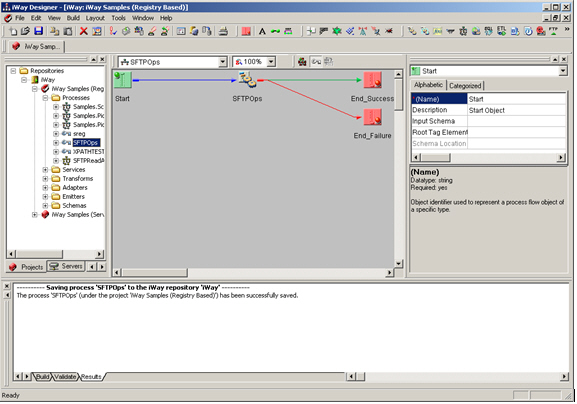
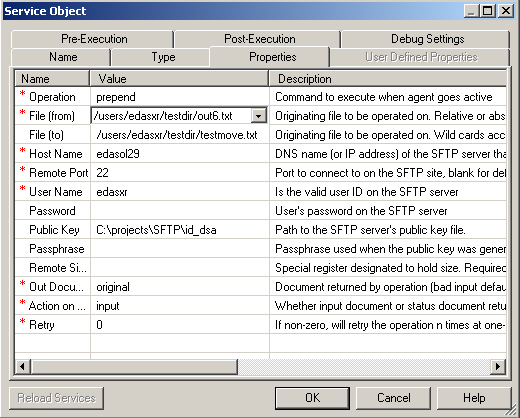
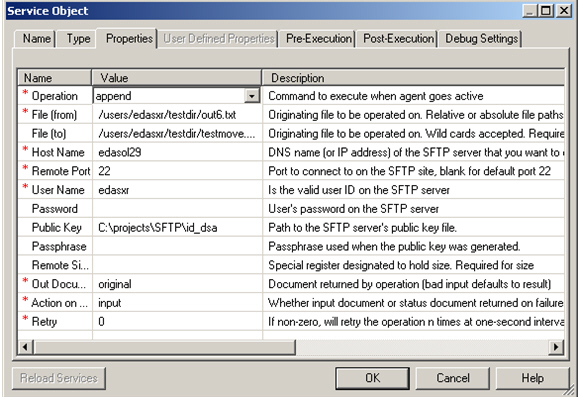
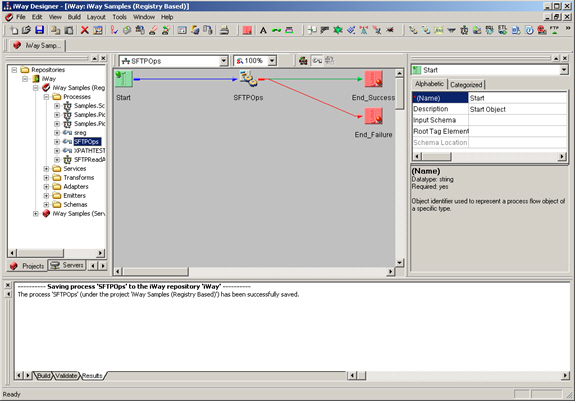
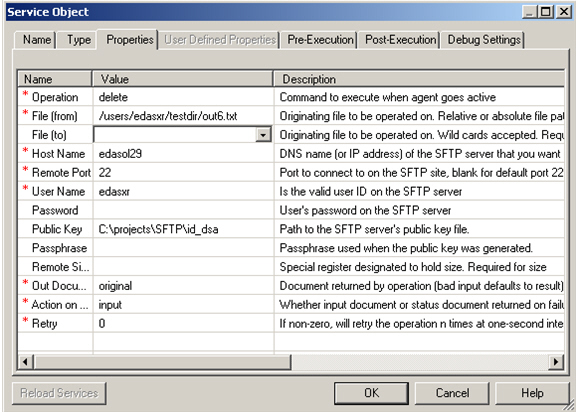
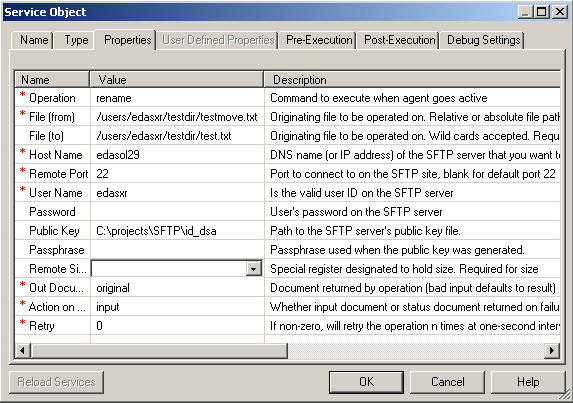
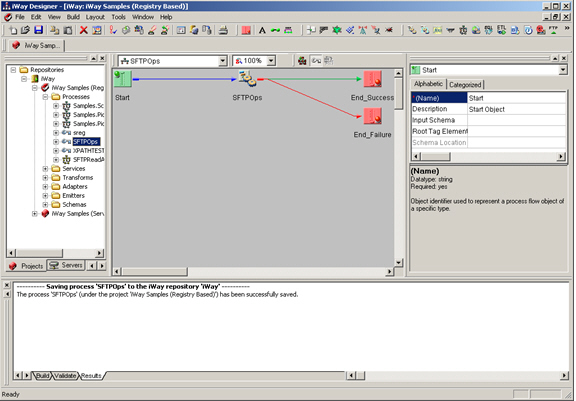
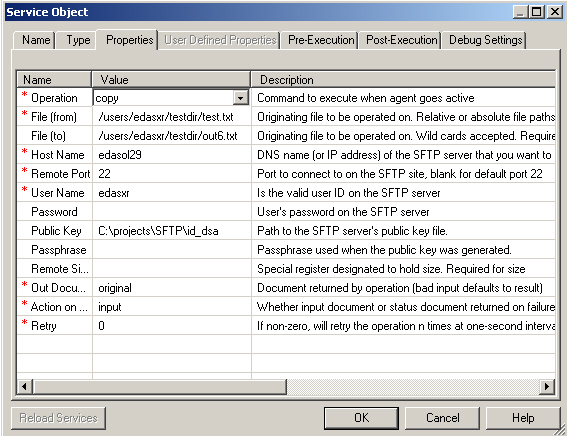
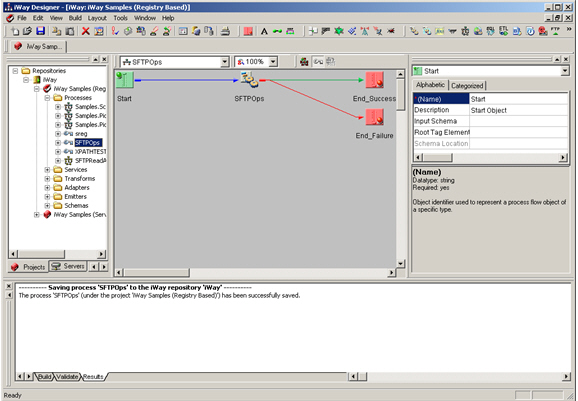
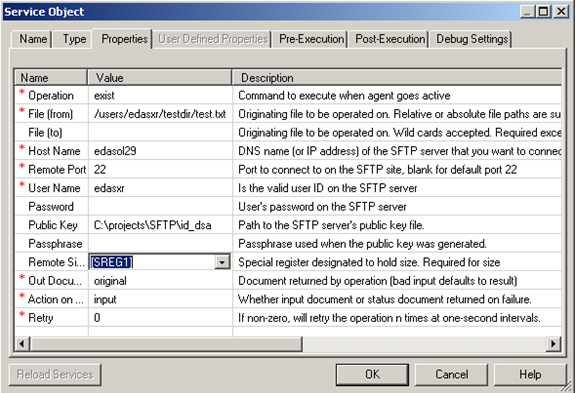
This section describes how to configure the SFTP listener.
The following table lists and describes the procedure for the SFTP Listerner.
|
Property Name |
Property Description |
|---|---|
|
Host Name |
Name of host machine where listener will contact service to obtain requests from. |
|
Remote Port |
Port to connect to on the SFTP site, blank for default port 22 |
|
Input Path |
Directory with optional pattern on SFTP host from which to retrieve files. A specific file name or DOS-style pattern) can be used. Do not use suffix in. |
|
Include Symbolic Links |
Set to true if you want the sftp listener to process the symbolic links |
|
Include Hidden Files |
Set to true if you want the sftp listener to process the hidden files |
|
Destination Directory |
Directory on SFTP host to return responses to |
|
Data, Signal or Streaming |
Data. Data file will be retrieved from the SSH server and maintained in memory while processed by the listener. Signal. Data file will be retrieved from the SSH server and stored locally (requires that the 'Local Store Directory' be filled in); a signal document will be generated by the listener. Streaming. A connection will be opened with the SSH server and data from the file will be retrieved and processed by the listener as needed. |
|
Local Store Directory |
Directory on the iWay server to save the files. Required when 'Data, Signal or Streaming' is set to Signal; otherwise this field is not used. |
|
Remove locally stored files |
Set to true if you want the SFTP listener to delete the file stored locally after it is processed |
|
Pending Queue |
Directory to hold documents which are to be retried later |
|
Suffix In |
Limits input files to those with these extensions. For example, enter "XML,in" to accept files with extensions "xml" and "in". Note that this is not case sensitive.Do not use '.'; use - to mean no extension, or * to mean any. |
|
Duration |
Maximum time that a document can remain in the retry pending queue |
|
Retry |
Interval between retrying pending requests |
|
Do not unzip ZIP files |
Pass ZIP files as a single file for processing (requires ACCEPT FLAT turned on) |
|
Bad File List |
Maintain a list of files with errors, preventing them from being re-accessed. If set, files will not be retried. |
|
User Name |
User ID on the SFTP server |
|
Password |
User's password on the SFTP server |
|
Private Key |
Path to the private key file for public-key authentication.. |
|
Passphrase |
Passphrase used to protect the Private Key |
|
Whitespace Normalization |
Specifies how the parser treats whitespace in Element content. Choose preserve to turn off all normalization as prescribed by the XML Specification.Choose condense to remove extra whitespace in pretty printed documents and for compatibility with earlier versions. |
|
Accepts non-XML (flat) only |
If true, listener expects flat (non-XML). Automatic parsing is not performed. |
|
Optimize Favoring |
Selection of memory is useful for large input document |
|
Multithreading |
Number of documents that can be processed in parallel |
|
Execution Time Limit |
Time limit for document execution(in seconds) before it is cancellation is attempted. (Also see system property "kill interval". This applies to agent stacks and sets a lower limit for process flows.) |
|
Polling Interval |
Interval at which to check for new input |
|
Default Java File Encoding |
Default encoding if incoming message is not self-declaring (i.e. XML) |
|
Agent Precedence |
Changes order by which engine selects agents. Normally Document overrides listener. This is used to manage iWay documents |
|
Always reply to listener default |
If true, the default reply definition is used in addition to defined replies |
|
Error Documents treated normally |
If true, error documents will get processed by any configured pre-emitters |
|
Listener is Transaction Manager |
If true, agents run within a local transaction managed by the listener |
|
Record in Activity Log(s) |
If set, activity on this channel will be recorded in the activity logs, else the activity will not be recorded. |
-
Construct an inlet consisting of an SFTP listener as shown
below:
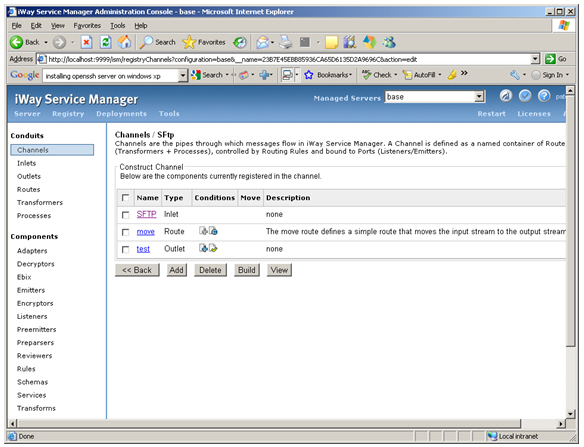
-
Construct a channel say, mySFTP consisting of the inlet, move
Route and a File emitter which writes the output file to a test
directory, say c:\test.
- Build and deploy the channel. Start the channel.
- Place an xml file on the directory /home/org on the SFTP host either using sftp commands or if the server is a windows machine by dropping it onto the folder.
- The SFTP channel processes this message and drops the file onto the directory c:\test on the iway client machine.