Each user is permitted to work only with a provided set of domains (for example, PartyMaster). This set is defined through the assigned roles type, called domain. You can create a role with the domain prefix (for example, domain.PartyMaster).
Each user should be assigned to at least one of the domain roles. The order of the domains can be edited in the Table Order tab in the administration pane.
To get the domain name that should be used as a part of the domain role, navigate to the iIMC administration pane and edit the corresponding table, as shown in the following image.
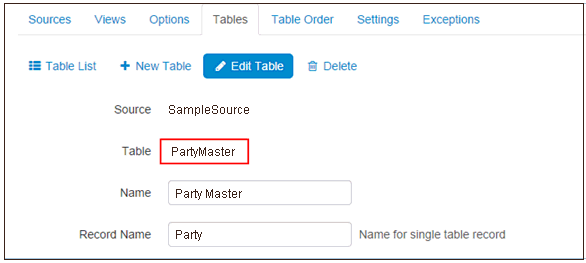
The value of the Table property should be used as part of the domain role after the period character (.), for example, domain.PartyMaster.
In the Roles of User section of the WSO2 Identity Server, a similar method is used, as shown in the following image:
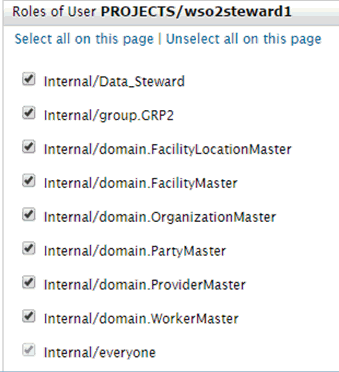
Note: After assigning users to a domain or any other roles, the user must log on again to the application.