Security for the iWay Service Manager (iSM) command facility is controlled and managed by the Access Control List (ACL) of iSM. For more information on this topic, see the iWay Service Manager Security Guide.
To issue a command, a user must be logged into the command facility with the appropriate authority. The main iSM Administration Console always runs at the administrator authority level. It is the responsibility of the system administrator to provide physical security to this console.
Command windows (telnet and SSH) are secured by their authentication realm, while each command issued by the Scheduler carries its own security. Access to the Scheduler is controlled by the system in which the schedule is created.
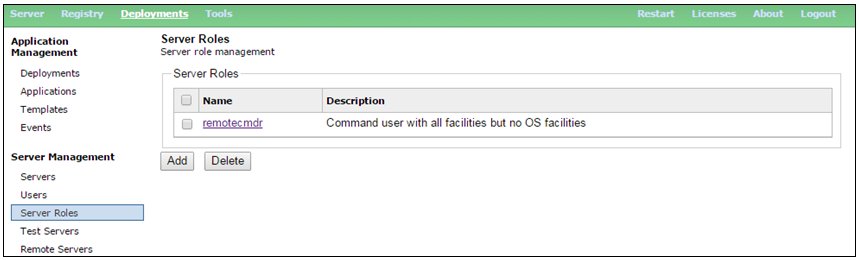
To quickly summarize the ACL facility, the system administrator first creates an ACL of a given name. Each user being authenticated by a security realm can be granted one or more such ACLs. In this example, we will create a list called remotecmdr, which will support some (but not all) commands.

Once this list is created, the specific commands (and in some cases groups of commands) that are available in that list are configured. In our example, the user issuing the command can perform all operations with the exception of the shell command and the set acl command.
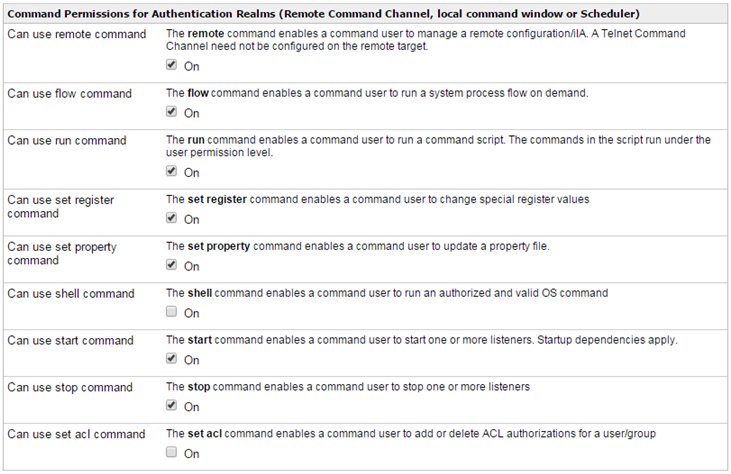
The user holding the remotecmdr list must be added to the realm (for example, LDAP) in order for the command user to log in.
| iWay Software |